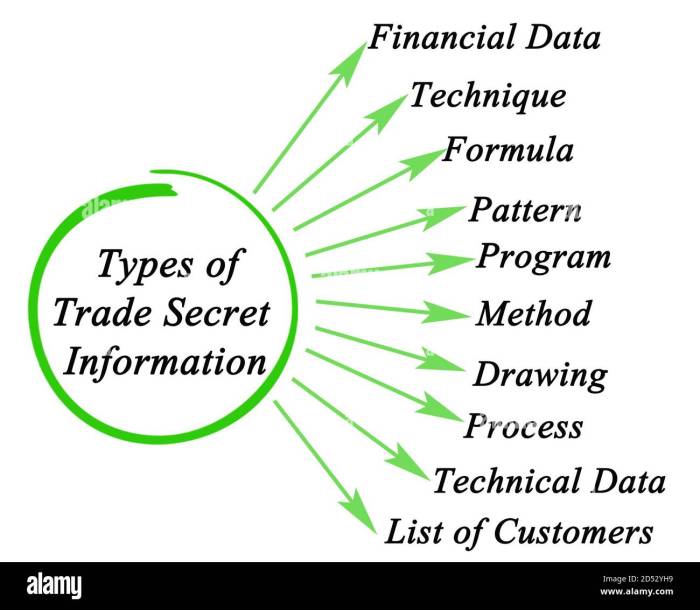
What is trade secert law – What is trade secret law? It’s a legal framework that protects confidential information that gives a business a competitive edge. Imagine a secret recipe, a unique customer list, or a cutting-edge marketing strategy. These valuable assets can be legally safeguarded under trade secret law, providing a powerful tool for businesses to maintain their competitive advantage.
This legal protection extends beyond simply keeping information confidential. Trade secret law Artikels specific requirements for qualifying information, defines how misappropriation occurs, and provides remedies for businesses whose trade secrets are stolen or misused. It’s a complex but crucial area of law that every business owner should understand.
Best Practices for Protecting Trade Secrets
Protecting trade secrets is crucial for any organization that relies on confidential information for its competitive advantage. A robust trade secret protection program should be comprehensive, encompassing various aspects of information security and legal compliance.
Designing a Comprehensive Trade Secret Protection Plan
A comprehensive trade secret protection plan should address the following key areas:
- Identification and Classification of Trade Secrets: The first step is to identify and classify all information that qualifies as a trade secret. This involves conducting a thorough inventory of confidential data, including formulas, designs, processes, customer lists, and other proprietary information. This process should be documented and regularly reviewed to ensure that the list of trade secrets remains up-to-date.
- Implementation of Security Measures: Once trade secrets are identified, appropriate security measures should be implemented to protect them. This includes physical security measures such as secure storage facilities, access control systems, and surveillance cameras. Additionally, logical security measures, such as strong passwords, encryption, and access controls, should be implemented to safeguard digital information.
- Employee Training and Awareness: Employees play a critical role in protecting trade secrets. Comprehensive training programs should be conducted to educate employees about trade secret law, the importance of confidentiality, and their responsibilities in protecting sensitive information. Regular reminders and updates should be provided to reinforce these principles.
- Non-Disclosure Agreements (NDAs): NDAs are legally binding contracts that require individuals to maintain the confidentiality of sensitive information. All employees, contractors, and other individuals who have access to trade secrets should be required to sign NDAs. These agreements should clearly define the scope of confidentiality, the obligations of the parties, and the consequences of breach.
- Regular Audits and Reviews: Regular audits and reviews should be conducted to assess the effectiveness of the trade secret protection program. This includes reviewing security measures, employee training, and NDA compliance. Audits can help identify vulnerabilities and areas for improvement, ensuring that the program remains effective in protecting trade secrets.
Best Practices for Safeguarding Confidential Information
- Limit Access: Only individuals with a legitimate need to know should be granted access to confidential information. This principle of “need-to-know” helps minimize the risk of unauthorized disclosure.
- Use Secure Communication Channels: When communicating sensitive information, use secure channels such as encrypted email, virtual private networks (VPNs), or secure messaging platforms. Avoid using public Wi-Fi or unsecure communication methods.
- Implement Strong Password Policies: Require employees to use strong passwords that are unique for each system or account. Implement password complexity requirements and enforce regular password changes.
- Data Encryption: Encrypt sensitive data both at rest and in transit. Encryption helps protect information from unauthorized access even if the data is intercepted or stolen.
- Regularly Update Software and Systems: Software and systems should be regularly updated to patch vulnerabilities and ensure the latest security features are in place. This includes operating systems, applications, and antivirus software.
- Establish a Secure Data Disposal Policy: Develop a secure data disposal policy to ensure that confidential information is properly disposed of when it is no longer needed. This may involve physical destruction of documents or secure deletion of electronic data.
Common Methods for Protecting Trade Secrets
| Method | Description | Example |
|---|---|---|
| Physical Security | Protecting physical assets that contain trade secrets, such as secure storage facilities, access control systems, and surveillance cameras. | Using a locked vault to store confidential documents or implementing a security system with keycard access to restricted areas. |
| Employee Training | Educating employees about trade secret law, confidentiality obligations, and best practices for protecting sensitive information. | Conducting mandatory training sessions on trade secret protection, including the importance of confidentiality, data security measures, and reporting suspicious activity. |
| Non-Disclosure Agreements (NDAs) | Legally binding contracts that require individuals to maintain the confidentiality of sensitive information. | Requiring all employees, contractors, and other individuals who have access to trade secrets to sign NDAs that clearly define the scope of confidentiality, obligations, and consequences of breach. |
| Data Encryption | Transforming data into an unreadable format using algorithms and keys, protecting it from unauthorized access. | Encrypting sensitive data stored on company servers, laptops, and mobile devices, as well as data transmitted over networks. |
| Access Control | Limiting access to confidential information based on individual roles and responsibilities. | Using role-based access control systems to ensure that only authorized personnel can access specific data or systems. |
| Watermarking | Embedding hidden identifiers or markings into digital documents or images to track their origin and prevent unauthorized copying. | Adding digital watermarks to confidential documents, such as design plans or marketing materials, to identify the source and discourage unauthorized distribution. |
Case Studies in Trade Secret Law: What Is Trade Secert Law

Trade secret law is a complex area of law with a rich history of litigation. Examining prominent cases provides valuable insights into the practical application of trade secret principles and how courts interpret and apply these principles in specific situations. By analyzing these cases, we can understand the nuances of trade secret law and its implications for businesses.
The DuPont Case
The DuPont case, formally known as *E. I. du Pont de Nemours & Co. v. Christopher*, is a landmark case in trade secret law. This case involved the theft of trade secrets for a secret process for making synthetic rubber. The case established the concept of “inevitable disclosure” as a basis for injunctive relief against potential trade secret misappropriation.
- The Facts: DuPont developed a secret process for making synthetic rubber. Christopher, a former DuPont employee, was hired by a competing company. DuPont argued that Christopher, due to his knowledge of the secret process, would inevitably disclose the trade secrets to his new employer.
- The Ruling: The court found that Christopher’s knowledge of DuPont’s trade secrets would inevitably lead to their disclosure to his new employer. The court granted an injunction prohibiting Christopher from working for the competing company.
- Significance: The DuPont case established the “inevitable disclosure” doctrine, which is still used today to prevent trade secret misappropriation. This doctrine allows courts to issue injunctions to prevent the disclosure of trade secrets even if there is no evidence of actual misappropriation.
The PepsiCo Case
The PepsiCo case, formally known as *PepsiCo, Inc. v. Redmond*, involved the misappropriation of trade secrets related to a new beverage product. The case highlights the importance of confidentiality agreements and the potential consequences of breaching them.
- The Facts: Redmond, a former PepsiCo employee, was hired by a competing company. Redmond had signed a confidentiality agreement with PepsiCo that prohibited him from disclosing PepsiCo’s trade secrets. PepsiCo alleged that Redmond would inevitably disclose PepsiCo’s trade secrets to his new employer.
- The Ruling: The court found that Redmond’s knowledge of PepsiCo’s trade secrets would inevitably lead to their disclosure to his new employer. The court granted an injunction prohibiting Redmond from working for the competing company.
- Significance: The PepsiCo case highlights the importance of confidentiality agreements and the potential consequences of breaching them. The case also demonstrates how courts will use the “inevitable disclosure” doctrine to prevent the misappropriation of trade secrets.
The Samsung Case, What is trade secert law
The Samsung case, formally known as *Samsung Electronics Co. v. Apple Inc.*, involved a dispute over the design of smartphones. The case demonstrates how trade secret law can be used to protect the design and functionality of products.
- The Facts: Apple sued Samsung for infringing on its trade secrets related to the design and functionality of its iPhone. Apple argued that Samsung’s Galaxy smartphones copied the iPhone’s distinctive design elements, including its rounded corners, grid-like icons, and the overall look and feel of the user interface.
- The Ruling: The jury found that Samsung had infringed on Apple’s trade secrets and awarded Apple billions of dollars in damages. The court also ordered Samsung to stop selling certain Galaxy smartphones in the United States.
- Significance: The Samsung case demonstrates how trade secret law can be used to protect the design and functionality of products. The case also highlights the importance of protecting trade secrets in the highly competitive technology industry.
Wrap-Up

In today’s competitive landscape, safeguarding confidential information is more important than ever. Understanding the intricacies of trade secret law empowers businesses to protect their valuable assets and maintain their competitive edge. Whether it’s a unique formula, a groundbreaking invention, or a strategic business plan, trade secret law provides a robust legal framework to safeguard these critical assets, fostering innovation and protecting the hard-earned success of businesses.
Detailed FAQs
What are some examples of trade secrets?
Examples of trade secrets include customer lists, marketing strategies, manufacturing processes, formulas, and software algorithms.
How long does a trade secret last?
Unlike patents and copyrights, trade secrets can last indefinitely as long as they remain confidential and provide a competitive advantage.
What happens if someone accidentally discloses a trade secret?
Accidental disclosure may not always constitute misappropriation, but it’s crucial to have strong confidentiality agreements and employee training in place to minimize the risk.
What are the remedies for trade secret misappropriation?
Remedies can include monetary damages, injunctions to stop the misappropriation, and even criminal prosecution in some cases.




